Ansible Basics
NAME HERE, TITLE HERE
COMPANY HERE
WHAT YOU WILL LEARN
Ansible is capable of handling many powerful automation tasks with the flexibility to adapt to many environments and workflows. With Ansible, users can very quickly get up and running to do real work.
In this presentation, we will cover:
- What is Ansible
- How Ansible Works
- Ad-Hoc Commands
- Playbook Basics
- Reuse and Redistribution of Ansible Content with Roles
- Ansible Tower
WHAT IS ANSIBLE AUTOMATION?
The Ansible project is an open source community sponsored by Red Hat. It’s also a simple automation language that perfectly describes IT application environments in Ansible Playbooks.
Ansible Engine is a supported product built from the Ansible community project.
Ansible Tower is an enterprise framework for controlling, securing, managing and extending your Ansible automation (community or engine) with a UI and RESTful API.
WHY ANSIBLE?
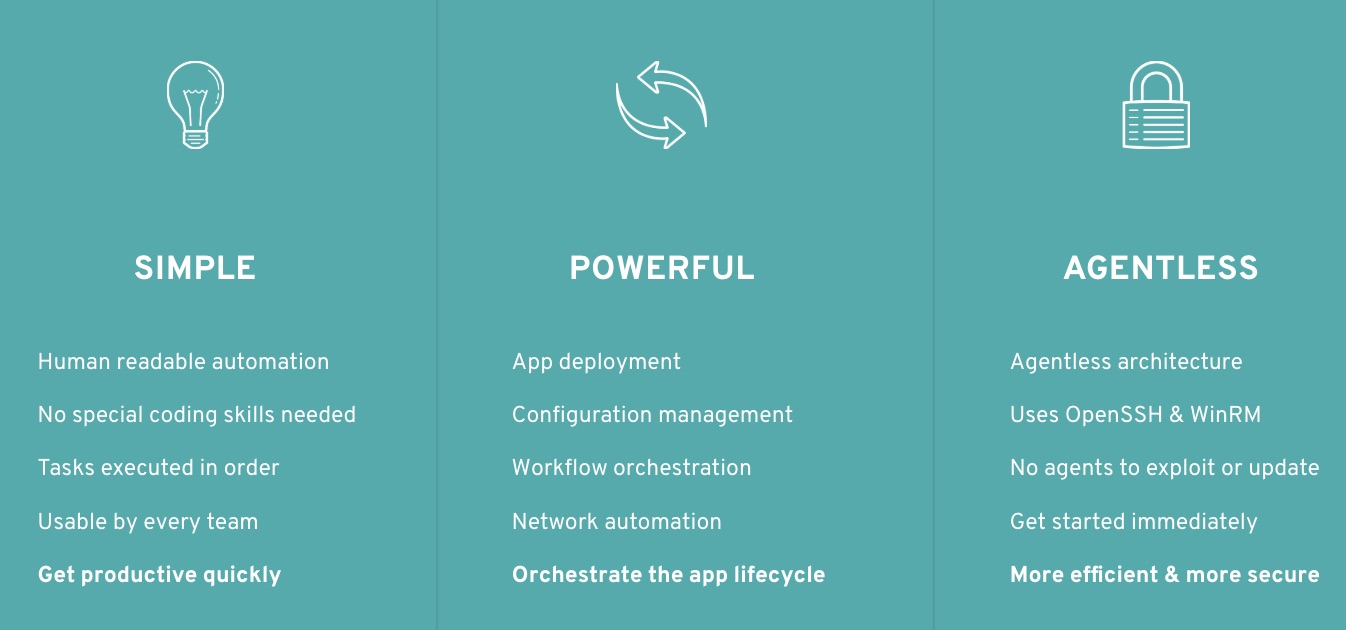
THE ANSIBLE WAY
CROSS PLATFORM – Linux, Windows, UNIX
Agentless support for all major OS variants, physical, virtual, cloud and network.
HUMAN READABLE – YAML
Perfectly describe and document every aspect of your application environment
PERFECT DESCRIPTION OF APPLICATION
Every change can be made by playbooks, ensuring everyone is on the same page.
VERSION CONTROLLED
Playbooks are plain-text. Treat them like code in your existing version control.
DYNAMIC INVENTORIES
Capture all the servers 100% of the time, regardless of infrastructure, location, etc.
ORCHESTRATION THAT PLAYS WELL WITH OTHERS – HP SA, Puppet, Jenkins, RHNSS, etc.
Homogenize existing environments by leveraging current toolsets and update mechanisms.
BATTERIES INCLUDED
Ansible comes bundled with hundreds of modules for a wide variety of automation tasks:
- cloud
- containers
- database
- files
- messaging
- monitoring
- network
- notifications
- packaging
- source control
- system
- testing
- utilities
- web infrastructure
COMMUNITY
THE MOST POPULAR OPEN-SOURCE AUTOMATION COMMUNITY ON GITHUB
- 34,000+ stars & 13,500+ forks on GitHub
- 4000+ GitHub Contributors
- Over 2000 modules shipped with Ansible
- New contributors added every day
- 1400+ users on IRC channel
- World-wide meetups taking place every week
- Ansible Galaxy: over 9,000 contributors and 18,000 roles
- 500,000+ downloads a month
- AnsibleFests, Ansible Automates, and other global events
ANSIBLE: COMPLETE AUTOMATION
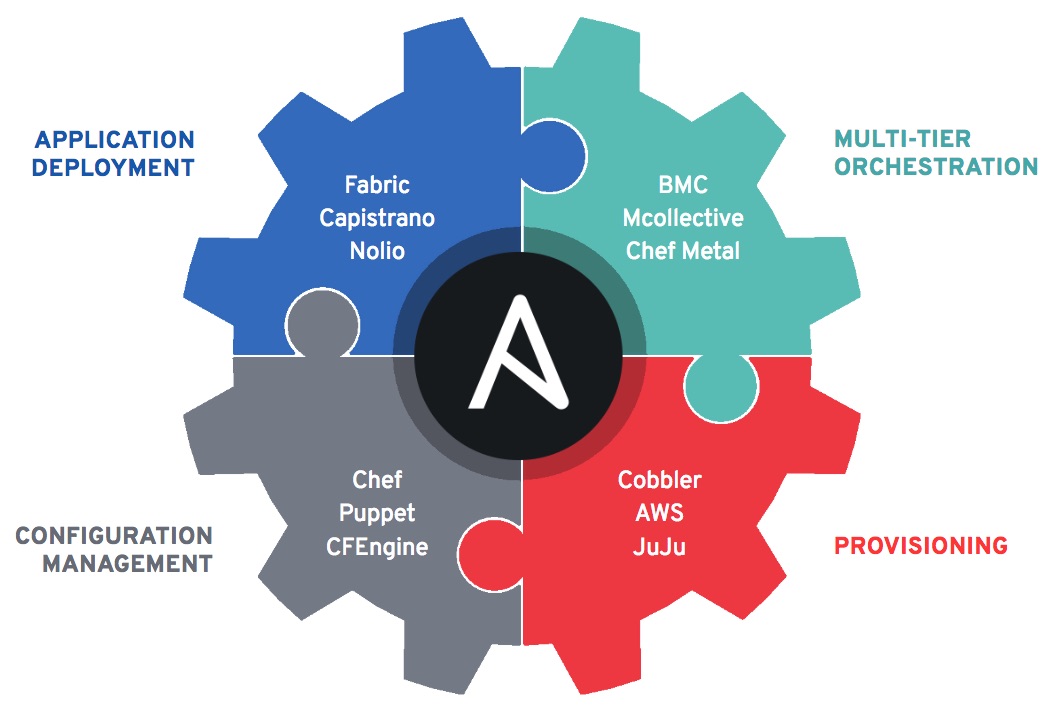
WHAT CAN I DO WITH ANSIBLE?
Automate the deployment and management of your entire IT footprint.
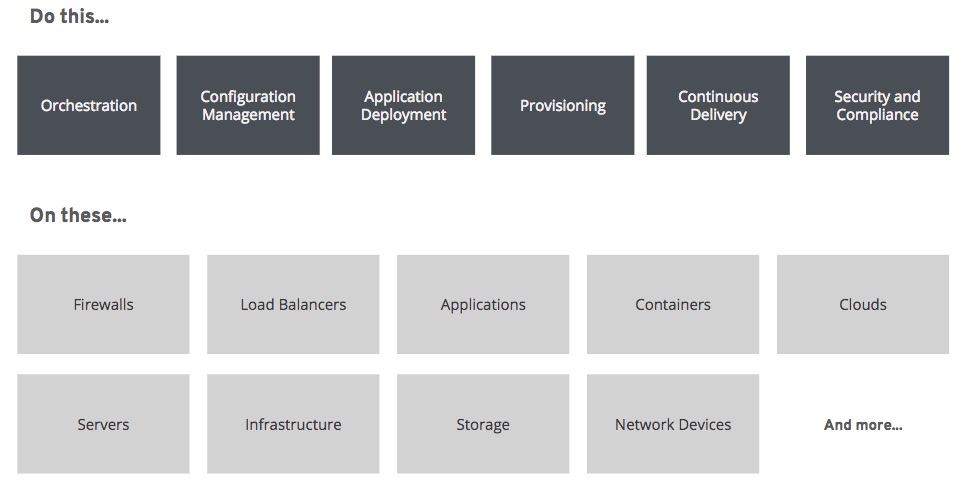
INSTALLING ANSIBLE
# the most common and preferred way of installation
$ pip install ansible
# install the epel-release RPM if needed on CentOS, RHEL, or Scientific Linux
$ sudo yum install ansible
# you will need the PPA repo configured
$ sudo apt-get install ansible
HOW ANSIBLE WORKS

MODULES
Modules are bits of code transferred to the target system and executed to satisfy the task declaration.
- apt/yum
- copy
- file
- get_url
- git
- ping
- debug
- service
- synchronize
- template
- uri
- user
- wait_for
- assert
MODULES
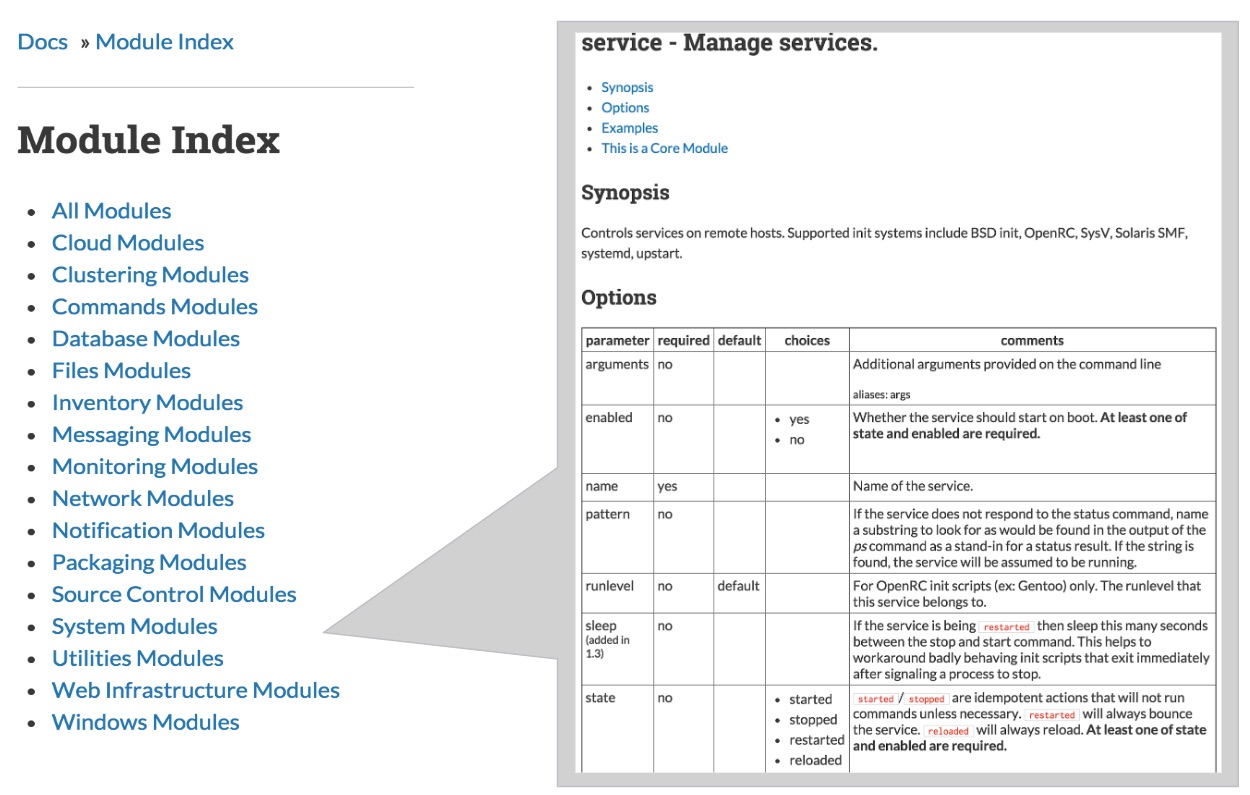
https://docs.ansible.com/ansible/latest/modules/modules_by_category.html
MODULES: RUN COMMANDS
If Ansible doesn’t have a module that suits your needs there are the “run command” modules:
- command: Takes the command and executes it. The most secure and predictable.
- shell: Executes through a shell like /bin/sh so you can use pipes etc. Be careful.
- script: Runs a local script on a remote node after transferring it.
- raw: Executes a command without going through the Ansible module subsystem.
NOTE: Unlike standard modules, run commands have no concept of desired state and should only be used as a last resort
AD-HOC COMMANDS
# check all my inventory hosts are ready to be managed by Ansible
$ ansible all -m ping
# run the uptime command on all hosts in the web group
$ ansible web -m command -a “uptime”
# collect and display the discovered for the localhost
$ ansible localhost -m setup
SIDEBAR: DISCOVERED FACTS
$ ansible localhost -m setup
localhost | success >> {
"ansible_facts": {
"ansible_default_ipv4": {
"address": "192.168.1.37",
"alias": "wlan0",
"gateway": "192.168.1.1",
"interface": "wlan0",
"macaddress": "c4:85:08:3b:a9:16",
"mtu": 1500,
"netmask": "255.255.255.0",
"network": "192.168.1.0",
"type": "ether"
},
INVENTORY
Inventory is a collection of hosts (nodes) against which Ansible can work with.
- Hosts
- Groups
- Inventory-specific data (variables)
- Static or dynamic sources
STATIC INVENTORY EXAMPLE
10.42.0.2
10.42.0.6
10.42.0.7
10.42.0.8
10.42.0.100
STATIC INVENTORY EXAMPLE
[control]
control ansible_host=10.42.0.2
[web]
node-1 ansible_host=10.42.0.6
node-2 ansible_host=10.42.0.7
node-3 ansible_host=10.42.0.8
[haproxy]
haproxy ansible_host=10.42.0.100
[all:vars]
ansible_user=vagrant
ansible_ssh_private_key_file=~/.vagrant.d/insecure_private_key
STATIC INVENTORY EXAMPLE IN YAML
all:
vars:
ansible_user: vagrant
ansible_ssh_private_key_file: ~/.vagrant.d/insecure_private_key
children:
web:
hosts:
node-1:
ansible_host: 10.42.0.6
node-2:
ansible_host: 10.42.0.7
node-3:
ansible_host: 10.42.0.8
VARIABLES
Ansible can work with metadata from various sources and manage their context in the form of variables.
- Command line parameters
- Plays and tasks
- Files
- Inventory
- Discovered facts
- Roles
VARIABLE PRECEDENCE
The order in which the same variable from different sources will override each other:
- Extra vars
- Set_facts/Registered vars
- Include_vars
- Include_params
- Role params
- Task vars (only for the task)
- Block vars (only for tasks in the block)
- Role vars
- Play vars_files
- Play vars_prompt
- Play vars
- Host facts
- Playbook host_vars
- Inventory host_vars
- Inventory file/script host vars
- Playbook group_vars
- Inventory group_vars
- Playbook group_vars/all
- Inventory group_vars/all
- Inventory file or script group vars
- Role defaults
TASKS
Tasks are the application of a module to perform a specific unit of work.
- file:A directory should exist
- yum:A package should be installed
- service:A service should be running
- template:Render a configuration file from a template
- get_url:Fetch an archive file from a URL
- git:Clone a source code repository
EXAMPLE TASKS IN A PLAY
tasks:
- name: add cache in directory
file:
path: /opt/cache
state: directory
- name: install nginx
yum:
name: nginx
state: latest
- name: restart nginx
service:
name: nginx
state: restarted
HANDLER TASKS
Handlers are special tasks that run at the end of a play if notified by another task.
EXAMPLE HANDLER IN A PLAY
tasks:
- name: add cache dir
file:
path: /opt/cache
state: directory
- name: install nginx
yum:
name: nginx
state: latest
notify: restart nginx
handlers:
- name: restart nginx
service:
name: nginx
state: restarted
PLAYS & PLAYBOOKS
Plays are ordered sets of tasks to execute against host selections from your inventory.
A playbook is a file containing one or more plays.
PLAYBOOK EXAMPLE
---
- name: install and start apache
hosts: web
vars:
http_port: 80
max_clients: 200
remote_user: root
tasks:
- name: install httpd
yum: pkg=httpd state=latest
- name: write the apache config file
template: src=/srv/httpd.j2 dest=/etc/httpd.conf
- name: start httpd
service: name=httpd state=started
ROLES
Roles are a packages of closely-related Ansible content that can be shared more easily than plays alone.
PLAYBOOK EXAMPLE
site.yml
roles/
common/
files/
templates/
tasks/
handlers/
vars/
defaults/
meta/
webservers/
files/
templates/
tasks/
handlers/
vars/
defaults/
meta/
This is how it looks from a project perspective. Not all of these directories need to be used, these are just standards that are available and ready to fill in with your tasks, handlers, variables, whatever you need for the particular role.
PLAYBOOK WITH ROLES EXAMPLE
# site.yml
---
- hosts: web
roles:
- common
- webservers
This is how you would call a role from the main playbook. It keeps everything simple and you can switch things out or delete easily without parsing through a huge list of tasks that you’ve made separately for every host type.
ANSIBLE GALAXY

If you’d like to check out our huge community site for Ansible roles, visit Galaxy.Ansible.com. You can sort through things by author name, stars, number of downloads, as well as other filters, and you can even share your own roles here as well.
WHERE TO FIND PLAYBOOK EXAMPLES
General Examples:
https://github.com/ansible/ansible-examples
Lightbulb:
https://github.com/ansible/lightbulb/tree/master/examples
Ansible + Vagrant:
https://github.com/geerlingguy/ansible-vagrant-examples
Here are some places where you can find some good playbook examples.
WHERE TO FIND PLAYBOOK EXAMPLES
Would you like to learn Ansible? It’s easy to get started:
ansible.com/get-started
Have you used Ansible already? Try Tower for free:
ansible.com/tower-trial
Want to learn more?
ansible.com/whitepapers
If you’d like to learn more about Ansible our Getting Started page is a great resource. Our documentation is also very thorough and well-written, so check that out as well. If you’re ready to try Tower you can visit our Tower Trial page, and you can also check out the whitepapers on our website!
Demo Time!
Show a playbook written out? Show roles? Tower?
more speaker notes here for those deep dive slides